Introduction
More than a million systems are now connected to the Internet, and something like 30 million people in 100 countries use Internet services. More than 100 million email messages are exchanged each day, along with countless files, documents, and audio and video images. Everyone is jumping on the Internet bandwagon. The Net is now reaching large and small businesses, government at all levels, school children, and senior citizens. The commercial world is rushing headlong into doing business on the Internet, barely pausing while technologies and policies catch up with their desire to go online. But, too few of the seekers after Internet wisdom and riches consider whether their businesses will be safe on the Net. Security has become one of the primary concerns when an organization connects its private network to the Internet.
Internet security is becoming a more, and more important term. Some people simply enjoy destroying other peoples work, while others might want to steal you company's secret data. Some people try to get real work done over the Internet, and others have sensitive or proprietary data they must protect. Network security is so vast a subject that it's almost impossible to understand completely. Hackers are always looking for new ways to intrude or wreak havoc on corporate networks, and it seems as if every time one problem is solved several more pop up. Firewalls are probably the first products that come to mind when you think of Internet security.
What is firewall?
A firewall is one way of protecting a computer network against the outside world. A firewall blocks all unauthorized communication between computers in an organization and computers outside that organization. It is also often used to prevent unnoticed and unauthorized export of proprietary information (11, p.1). It is a system or group of systems that enforces an access control policy between two networks. The firewall determines which inside services may be accessed from the outside, which outsiders are permitted access to the permitted inside services, and which outside services may be accessed by insiders.
If the data on your network is like a castle, how far do you let people into the castle, and what do you allow them to do once inside? Firewall will work on it, same as security guard (8, p. 1).
Types of Firewall:
There are two different kinds of firewalls.
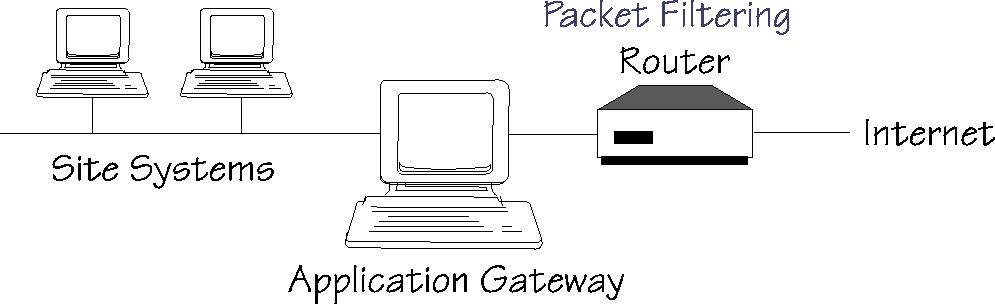
Packet Filtering:
Packet filtering firewalls works at the network level.
They examine each packet that attempts to enter or leave the network and
compare it with a programmed list of criteria. In typical configurations,
packets are blocked unless they are specifically allowed. Packets
are first checked and then either dropped or allowed to enter based on
various rules and specified criteria.

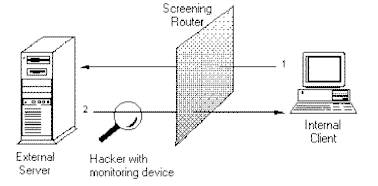
A screening router is the basic component of most firewalls. A screening router can be a commercial router or a host-based router with some kind of packet-filtering capability. Typical screening routers have the ability to block traffic between networks or specific hosts, on an IP port level. Some firewalls consist of nothing more than a screening router between a private network and the Internet (10, p. 1).
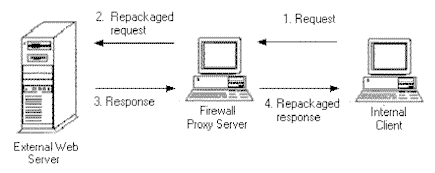
Proxy Sever Gateways:
The highest level of protection today is provided by
application-level proxy servers. Gateways work at a higher level
in the protocol stack to provide more opportunities for monitoring and
controlling access between networks. A gateway is like a middle-man,
relaying messages from internal clients to external services. The
proxy service changes the IP address of the client packets to essentially
hide the internal client to the Internet, then it acts as a proxy agent
for the client on the Internet.
Using proxies reduces the threat from hackers who monitor network traffic to collect information about computers on internal networks. The proxy hides the addresses of all internal computers. Traditionally, using proxies has reduced performance and transparency of access to other networks. However, current firewall products solve some of these problems (8, p. 1).
There are two types of proxy servers:
1. Circuit Level Gateway:
This type of proxy server provides a controlled network
connection between internal and external systems (i.e., there is no "air-gap").
A virtual "circuit" exists between the internal client and the proxy server.
Internet requests go through this circuit to the proxy server, and the
proxy server delivers those requests to the Internet after changing the
IP address. External users only see the IP address of the proxy server.
Responses are then received by the proxy server and sent back through the
circuit to the client. While traffic is allowed through, external
systems never see the internal systems. This type of connection is
often used to connect "trusted" internal users to the Internet (8, p. 1).
2. Application Level Gateway:
An application-level proxy server provides all the basic
proxy features and also provides extensive packet analysis. When
packets from the outside arrive at the gateway, they are examined and evaluated
to determine if the security policy allows the packet to enter into the
internal network. Not only does the server evaluate IP addresses,
it also looks at the data in the packets to stop hackers from hiding information
in the packets (8, p. 1). A typical application-level gateway can
provide proxy services for applications and protocols like Telnet, FTP
(file transfers), HTTP (Web services), and SMTP (e-mail).
The disadvantage of an application level gateway is that
you need a specialized program for each application you want to use through
the gateway. This means that you can't offer every service through
your gateway, and it takes time to configure a new service for use on the
gateway (10, p. 1).
Firewall Policies
If someone can find a hole in your firewall, then the
firewall has failed. Security policies must be outlined in advance
so administrators and users know what type of activities are allowed on
the network.
Examples of outlines are:
In deciding to build a firewall, answer to the following questions might help you decide whether it has the resources to build and operate a successful firewall:
These are seven of the best-selling firewall systems in the market. All of them provided excellent security in our network tests, but they offer different interfaces and features. (This information has been tested in February 1997 by Brooks Talley)
CyberGuard Firewall 3.0
CyberGuard Firewall 3.0 is the most improved product
in this comparison. CyberGuard offers a solid, turnkey firewall solution
that is particularly easy to administer and comes bundled with installation
services. Its support for high-end multiprocessing Intel PCs also
makes it a good candidate for an Intranet firewall because it can support
10Base-T speeds and above.
CheckPoint Firewall-1 2.1
CheckPoint is a very solid product with a history of
reliability and a refined user interface. The addition of a remote
administration tool that runs on Microsoft Corp.'s Windows 95 and can control
Unix- and Windows NT-based, CheckPoint firewalls is a great improvement.
CheckPoint is a good solution for government sites that need remote administration
capabilities.
Sidewinder Security Server 3.0
Side-winder is similar to CyberGuard's, but Secure Computing
doesn't supply a backup tape or boot disks. It is another good choice
for government sites that need re-mote administration of firewalls.
This turnkey package was flexible and easy to administer, but we wish it
came with backup materials in case of a network crash.
Gauntlet Internet Firewall
It is one of the more basic firewall implementations,
lacking a lot of the features that some others have. For a basic
firewall that doesn't need to pass esoteric data types, Gauntlet is an
excellent choice. Its proxies work easily and quickly.
SmartWall 3.3.1
It is ok but for organizations that need more control
over what traffic is allowed in and out, it's not enough.
Black Hole 3.0
Black Hole's administration wasn't as complete as CheckPoint's,
but it still had the kind of modern user interface that really helped us
use the firewall. Black Hole offers one of the easiest and most automated
installation processes.
Eagle NT
Eagle is one of the few firewalls available for the Windows
NT platform. It features strong integration with NT's domain security
and prevents unauthorized processes, but the package feels more like Unix
than Windows NT (9, p. 1).
Cost of firewalls
The cost of a firewall which a company can incur for a
firewall can range from $10,000 to $100,000. Including hardware and
software. The cost of a system depends on the wants of the company
(11, p. 1).
Summary
Firewalls are a good means of security but they cannot
protect against everything. Firewalls cannot protect against attacks
that do not go through the firewall. They cannot protect against
viruses. There are some people who are intelligent enough to find
a loophole through the firewall. No security system is 100% secure;
however, firewalls enhance host security by funneling attackers through
a narrow gap where there is a chance of catching or detecting them first
(11, p. 1).
BIBLIOGRAPHY
Books:
1. Derfler, Frank (1998). Using Network. Indiana: Que.
2. Goncalves, Marcus (1997). Firewalls Complete. New York: McGraw-Hill.
World Wide Web sites:
3. Martha, T. Effective Firewalls. http://www.utexas.edu/courses/kincaid/tyler/effect.html
(1996, March 24)
4. Martha, T. Types of firewalls. http://www.utexas.edu/courses/kincaid/tyler/type.html
(1996, March 24)
5. Mecklermedia Corporation. Firewall. http://www.pcwebopedia.com/firewall.htm
(1997, May 29)
6. O'Reilly & Associates, Inc. Building Internet Firewalls. http://www.oreilly.com/catalog/fire/desc.html
(1998,
July 2)
7. Semeria, C. Internet Firewalls and Security. http://www.3com.com/nsc/500619.html
(1998, July 1)
8. Sheldon, Tom. General Firewall White Paper. http://www.ntresearch.com/firewall.html
(1996, November)
9. Tallay, Brooks. Seven Firewalls That Keep Your Network Safe. http://www.fcw.com/pubs/gbb/1997/0203/gbb-firewall-2-3-1997.html
(1997, February 3)
10. Trosvik, H. Firewalls. http://www.uio.no/~hege/in312/firewall.html
(1998, June 29)
11. Woodcock, Ph.D. Mark. FIREWALLS. http://www.cs.umbc.edu/~woodcock/cmsc482/proj1/firewall.html
(1995, October 26)
12. Wack, J. Internet Firewalls Frequently Asked Questions. http://www.telstra.com.au/pub/docs/security/800-10/node81.html
(1995, February 3)
13. Wack, J. Introduction to Firewalls. http://www.telstra.com.au/pub/docs/security/800-10/node30.html
(1995, February 3)